Understand the unseen risks of third-party OAuth integrations and how AppGuard360 identifies them before they cause harm.
Our Latest Resources
Core capabilities that help you see, understand, and fix risks.
The Hidden Danger of “Connected Apps” in Microsoft 365—and How to Fix It
Microsoft 365 / Entra ID connected apps (OAuth) power everything from e-signatures and CRM sync to ticketing and file automation. The danger is that “helpful” integrations can quietly accumulate broad access—mail, files, directory data—without ongoing oversight. When something goes wrong, the cost shows up fast. That’s why the ROI of Microsoft 365 app governance is now one of the simplest, most defensible security investments you can make. ROI of Microsoft 365 App Governance App governance...
Connected Apps Are the New Attack Surface in Microsoft 365 (And It’s Not Mainstream Yet)
Microsoft 365 connected apps security: what IT admins need to know Microsoft 365 connected apps security is now a core admin priority because OAuth permissions can create standing access to mail, files, and directory data until app grants are reviewed and revoked. Yet most Microsoft 365 security conversations still orbit the same center of gravity: passwords, MFA, and user sign-ins. But attackers are quietly shifting one layer deeper—toward Microsoft 365 / Entra ID connected apps (OAuth) ....
How OAuth Apps Can Expose Your Microsoft 365 Tenant
Understand the unseen risks of third-party OAuth integrations and how AppGuard360 identifies them before they cause harm. OAuth Apps Are One of the Most Overlooked Risk Surfaces in Microsoft 365 Most Microsoft 365 security incidents don’t start with malware. They start with legitimate access — granted to OAuth apps that quietly retain permissions long after anyone remembers approving them. OAuth integrations are designed for convenience. Over time, that convenience becomes persistent,...
Webhook Security: Discovery, Validation, Monitoring
Webhooks quietly move sensitive data between systems — often with no visibility, no ownership, and no monitoring. They power automation, SaaS integrations, and modern workflows, but they also create a blind spot inside Microsoft 365, Azure, and third-party platforms. This guide explains how webhooks work, why they’re risky, and how to govern them using a practical framework built on discovery, validation, and continuous monitoring . Subscription required • Cancel anytime What Is a Webhook...
Microsoft 365 Connected Apps Risk Assessment & Governance
Identify risky Microsoft 365 / Entra ID connected apps (OAuth), understand their permissions, and enforce ongoing governance — without spreadsheets or guesswork. Microsoft 365 connected apps governance is the process of maintaining visibility and control over third-party and internal applications that access Microsoft 365 through OAuth. These connected apps often operate with delegated or application-level permissions and do not rely on an interactive user session. Modern Microsoft 365...
OAuth Security for Microsoft 365: The Complete Guide
Understand OAuth apps, permissions, service principals, and webhooks — and how to control them without breaking the business. OAuth has become one of the most powerful — and least understood — access paths into Microsoft 365 environments. Modern businesses rely on cloud applications to automate workflows, integrate platforms, and improve productivity. Most of those applications connect using OAuth. Once approved, they can operate quietly in the background, often with broad access to email,...
Microsoft 365 Device Code Phishing: Why MFA Isn’t Enough (and What to Do Next)
A recently reported attack campaign highlights a growing weakness in how organizations think about identity security in Microsoft 365. According to a December 2025 report published by The Hacker News , threat actors linked to Russia have been abusing Microsoft 365 device code authentication to gain access to accounts while bypassing traditional phishing defenses and MFA protections. Source: The Hacker News — “Russia-Linked Hackers Use Microsoft 365 Device Code Phishing to Bypass MFA” ...
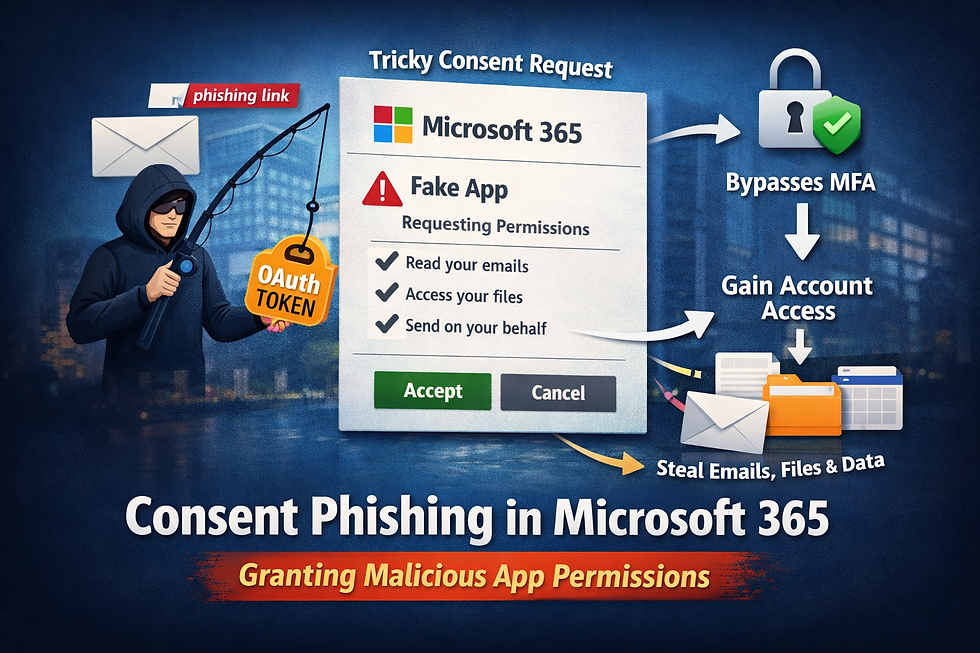
Consent Phishing in Microsoft 365: How It Works & How to Prevent It
Consent phishing in Microsoft 365 is when an attacker tricks a user into granting a malicious application access via OAuth (Open Authorization) instead of stealing a password. The fake app presents a consent screen requesting risky scopes. Once approved, the attacker gets long-lived token access through a service principal—often bypassing MFA. Quick definition Consent phishing—also called an illicit consent grant —is when an attacker gains access without stealing a password by persuading a...